Improve Security with NubOps
Quickly detect security risks caused by misconfigurations
Have you ever wondered this?
- •If the settings in your Azure environment are secure
- •Which endpoints are exposed to threats originating from the Internet
- •If others are following security best practices and recommendations
- •If there was an easier way to review solutions before giving approval to deploythem in the production environment
Your digital IT security expert
NubOps helps you out by collecting information automatically and checking configuration settings for you. Verifying that hardening has been performed is impossible to do manually in large environment, that change day-to-day, but it also always wastes time. Analyzing the security state in your Azure environment has to be done using automation. You should go through the audit findings and instead spend your valuable time on making a decision on what needs to be done to reduce risk.
IT security risk analysis and remediation
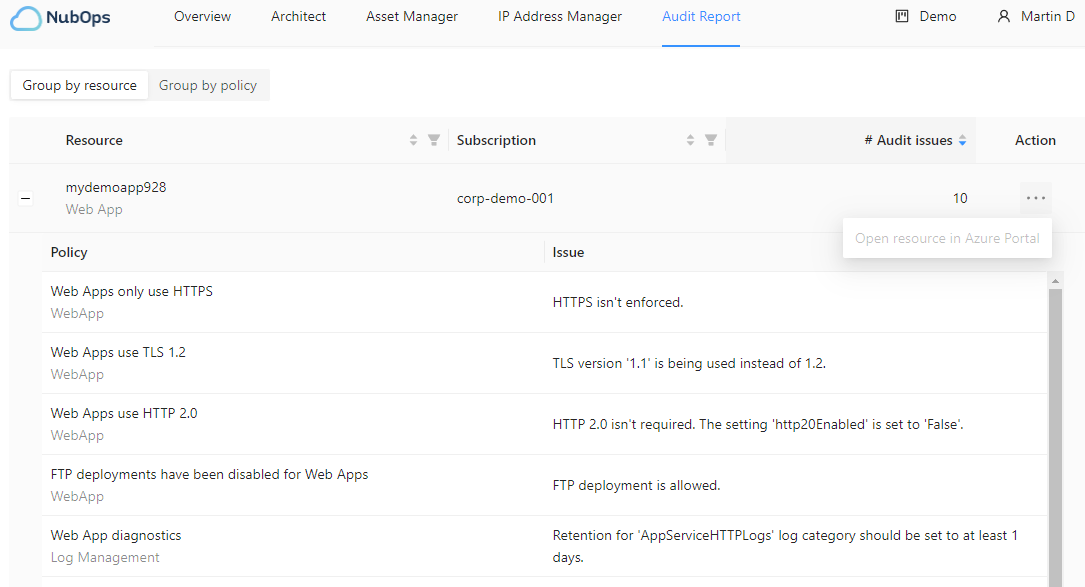
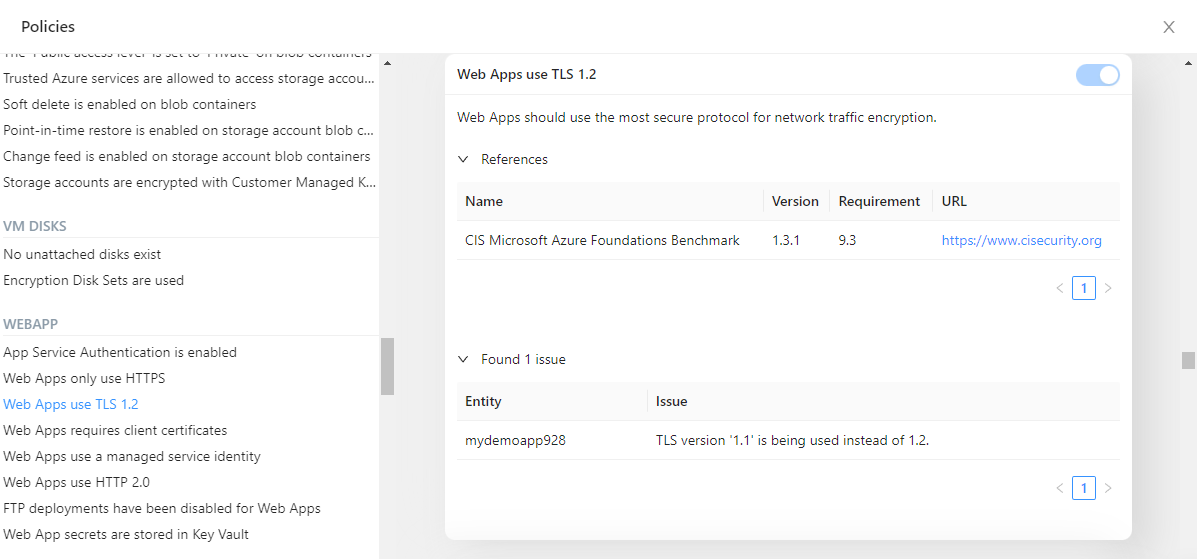
The Audit report feature is used to identify resources where configuration changes could improve security or governance. The feature is based around numerous policies where each policy has been developed to find specific information about how resources have been configured.
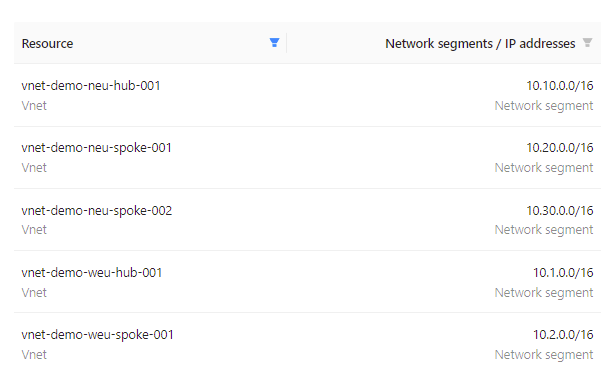
Having access to detailed information is necessary when evaluating the probability of a security incident occurring. NubOps can also be used to go through all assets from a networking perspective, as that provides a helpful context regarding possible attack vectors. Use the IP Address Management feature to go through all the endpoints which might permit be inbound traffic.
The Asset Manager feature helps you analyze App Registrations that have been assigned access to, and permissions in, your Azure Active Directory tenant. Also use it to review which app registrations require renewed consent or which can be deleted. App Registrations credentials could be used by someone outside your organization to enumerate sensitive information from your Azure Active Directory tenant, which then could be used in an attack. Especially if excessive permissions have been assigned, either in privilege (allowing write operations) or in scope (too broad access).