Audit feature has been released into public preview
31 August 2022
We’ve now released a new feature called “Audit report”. The purpose of this feature is to help with analysis of all the audit issues that NubOps detects based on the policies that are enabled. It’s also easy to open up a separate web page that leads to the resource in the Azure portal. This makes it easy to reconfigure different resources in a shorter amount of time.
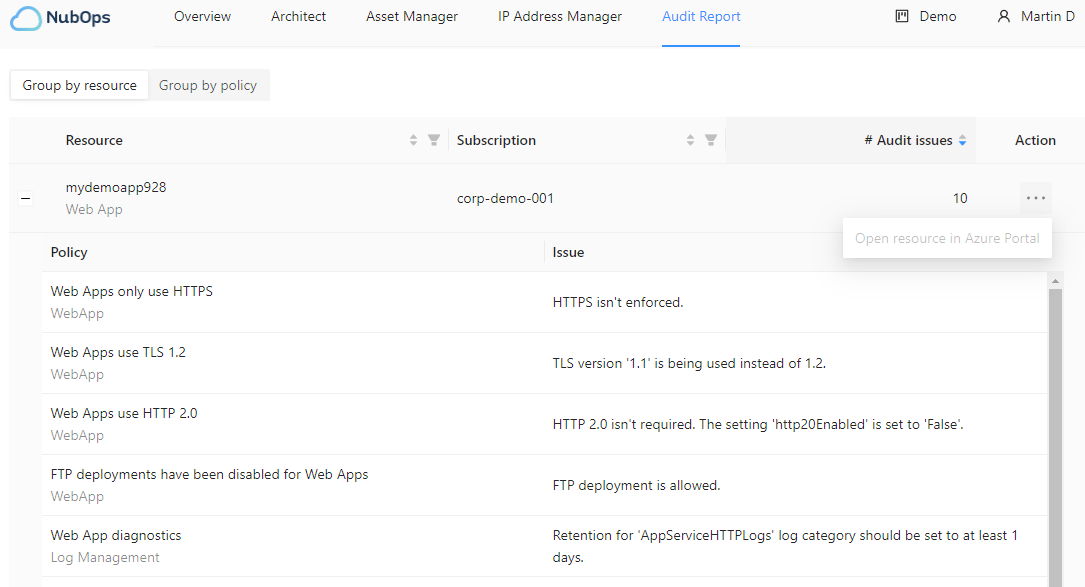
The “Group by resource” view
When multiple policies applies to a resource type, such as an web app, it’s now possible to review all detected audit issues in one place in the “Group by resource” view. This view is shown by default. From this view you can then click on “Open resource in Azure” to open a separate brower for the Azure portal. This means that you can perform mitigating actions to address anything that you consider to be misconfigured, insecure or that could be improved.
The “Group by resource” view has filtering options based on resource type, subscription and the total number of issues. This means that you can focus on specific resource types that you are responsible for, focus on the most sensitive subscriptions and also to focus on resources which have the most issues.
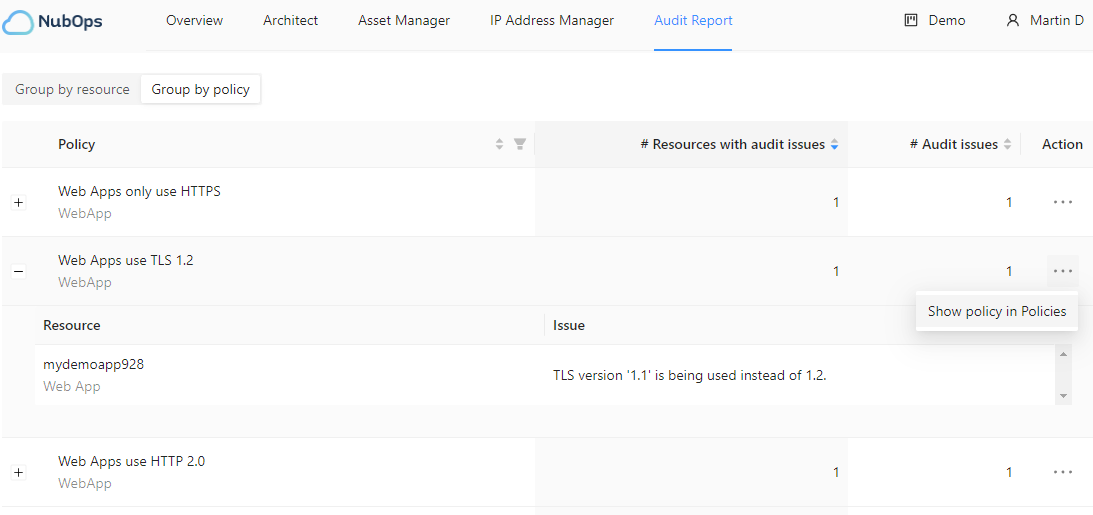
The “Group by policy” view
As a single policy can detect issues in multiple resources it’s also possible to select “Group by policy” and see all non-compliant resources of that specific resource type which, for one reason or another, fails the check done by the policy. The purpose of this is that it makes it possible to see how widespread an issue is across subscriptions. This could indicate if a potential problem needs to be addressed in other non-technical ways.
The “Group by policy” view has filtering options based on resource type, how many resources have at least one issue and also the total number of issues all resources have. This means that you as an example can see that five storage accounts in totalt are non-compliant with the enabled policies. Then you can see exactly how many issues these five storage accounts have since they might fail a different amount of policy audits.
Policy setting improvements
The “Policies” settings has also been improved so that it’s now possible to see which, and how many, resources are non-compliant as you enable a policy. This is only possible if you select the “Custom” policy ruleset. The purpose here is to make it easier to decide if you want to enble a policy or not. Even if you don’t want to enable it you can always use it to check what the number of non-compliant resources would look like.